
Securing Vehicle Data: Implementing Standardization for Safe Access and Mitigating Cyber Threats
With vehicles becoming a popular attack surface, it’s important to address how to mitigate bad actors and breaches in an age where nearly everything we touch is collecting troves of data. The simple answer, is standardization – a method which our most secure industries use (such as the military and banks) yet the automakers will not implement.
Bad actors are breaching current vehicles and vehicle manufacture systems at an alarming rate.
In 2022, the number of cyber-attacks in the automotive industry continued to increase, some of which amplified car thefts to nearly 80,000 vehicles per month, according to a 2022 National Insurance Crime Bureau report. According to the media platform Government Technology, half of all automotive cyberattacks in history occurred in 2021 alone — up nearly 140% from 2020. Since 2021, malicious attacks have surpassed the vulnerabilities detected by researchers, cyber security engineers, and analysts who are tasked with uncovering and reporting security vulnerabilities. When the threshold of malicious attacks versus vulnerability detection is surpassed, it indicates that the good guys are losing the battle.
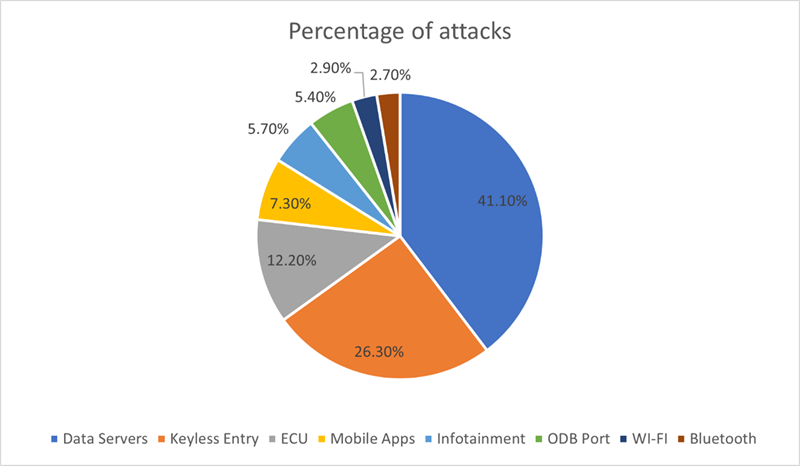
The following chart shows that the hacker’s primary targets are the OEM backend servers. Hackers know they can obtain more money and data by ransoming these servers. As vehicles become more dependent on cloud services, the security of OEM backend servers becomes more critical. This prompts the question, are we approaching a point where we must ask if the vehicle is drivable without network connectivity? Regardless, the fact is that hackers are less interested in hacking individual vehicles other than for the purpose of stealing them than they are in hacking OEM servers. It is clear from the following pie chart that hackers want to attack OEM servers and steal vehicles. There has been only one reported instance where an OEM server was hacked from a vehicle. That incident involved a Japanese manufacturer in which a cellular SIM card was taken from a vehicle and used to connect a laptop to the OEM server. Due to a lack of basic security practices on the OEM's part, the hacker was able to derive the username and password from readily available information. This resulted in the manufacturer’s telematics systems being offline for months.
The pie chart also indicates that hackers are not particularly interested in OBDII data. OBDII data is the data that the aftermarket needs to receive locally or remotely to diagnose, repair and maintain vehicles. Accessing maintenance and repair data should not depend on the access method if done safely and securely. If already-existing ISO standards were implemented, along with a standards-compliant security architecture, it could reduce, if not eliminate, the types of security breaches reported since 2018. It would also ensure that necessary data could be accessed from vehicles in a safe and secure fashion only by certified, authenticated, and authorized vehicle owners and service providers.
Source: Intertek https://www.intertek.com/blog/2023-01-05-automotive-cybersecurity/
If the security standards were adopted, diagnostics and maintenance data could also be segmented from other data types and accessed only by registered, certified, authenticated, and authorized systems, tools, and technicians – keeping drivers on the road safer, longer, and ensuring their Right to Repair.
Dark Web
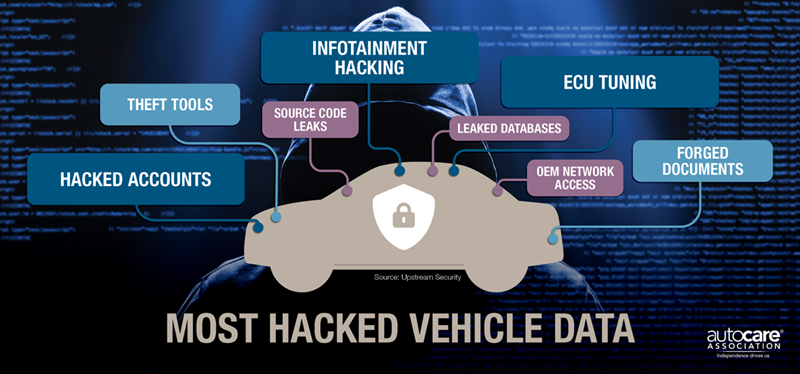
An excellent way to identify security threats and breaches is on the Dark Web. The Dark Web is where illicit and malicious activity transpires. It is the right place to gauge the cybersecurity threat by seeing what is being sought after and what is being sold, as indicated in the following diagram. Vehicle software source code and the data stolen from OEM databases top the list. As you would expect, the other information includes infotainment hacking, primarily used to obtain free services, and ECU/chip tuning hacks. The other items are the more traditional hacking items like identity theft and forged documents like fake insurance cards and driver’s licenses. If the owners do not pay the ransom, this data finds its way to dark websites and open-source platforms, which bad actors then access and repost. Beyond the ECU chip tuning that has been around well before cars were connected to anything, the focus on the Dark Web is car theft and OEM server hacking, not diagnostic and maintenance data.
One might assume vehicle cyber-attacks mainly occur against older vehicles, but the following incident involving a 2021 Korean-manufactured electric vehicle may make you reconsider. The vehicle owner, known as greenluigi1, obviously was not a typical owner; he was well versed in Linux programming and could access the firmware on the vehicle’s head unit, reverse engineer the app framework, and even create his own apps. He even wrote a tutorial on how anyone can create their own apps. This incident is an example of “security by obscurity,” when manufacturers build backdoors into their systems and hope no one will discover them, only to see them later, on Reddit or Hackaday. These backdoors can be hidden areas on a touchscreen or actions “such as opening the hood and connecting the driver's seatbelt that allows access to sensitive areas like a login prompt to the system software operating system.
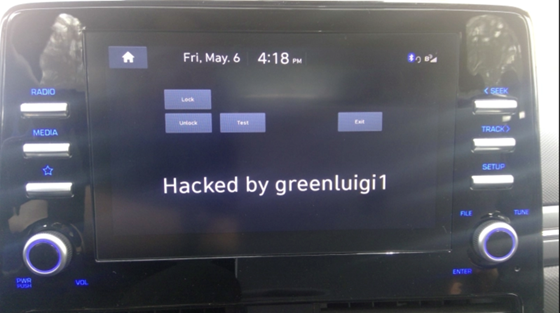
(Source: https://hackaday.com/2022/07/18/hacker-liberates-hyundai-head-unit-writes-custom-apps/)
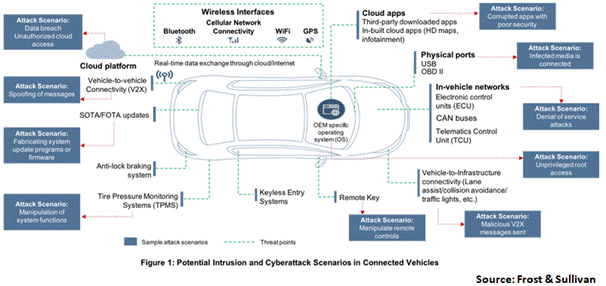
Attack surfaces
Attack surfaces are all possible points, or attack vectors, where an unauthorized user can access a system, extract data, deny services, or perform other malicious acts. The attack surfaces of vehicles are increasing as the vehicles continue to progress towards Software Defined Vehicles (SDV). The following diagram identifies nearly all the existing vehicle attack surfaces, apart from the EV charging point. These surfaces are diverse and vary in form, function, and criticality.
Electric Vehicle Challenges
As the United States becomes more dependent on EVs, the power grid could evolve into a single point of failure for all transportation. The EV charging interface has become a critical target since it presents a potential attack surface to charging systems and the power grid. When the charging services providers, vehicle manufacturers, and the US government identified this as a critical concern, they worked collectively to form an SAE task force to develop standards for securing this critical interface. The standard they created is SAE TEVEES18E, and it is highly similar, to say the least, to the ISO 21177 standard that the aftermarket has been pointing to as a solution for providing safe, secure, and standardized access to vehicle maintenance and repair data. This begs the question, why isn’t securing the in-vehicle network critical enough to garner the same attention of the OEMs? Shouldn’t this same architecture and rigor be applied for all interfaces to the vehicle as recommended by the Intelligent Transport Systems ISO standards?
Who Owns the Vehicle Data?
A system this diverse and complex requires an advanced security architecture that can manage and adapt to both current and future security challenges, one that can provide the necessary security and yet allow consumers the ability to choose what data they share and with whom they share it. In 2018, 2019, 2021, and 2022, the Auto Care Association, along with some of its members, have demonstrated, at various levels, an architecture that we believe can provide the necessary security and allow for consumer choices in who has access to their data. An old axiom states that as security increases, productivity decreases, meaning that a fully secured vehicle would be locked in a vaulted garage with no connectivity and not allowed to move. This does not have to be the case. Individuals and systems accessing vehicle data can be registered, certified, authenticated, and authorized based on international security standards. This security architecture is based on ISO 21177, ISO 21184, ISO 21185, and IEEE 1609.2. and are being prescribed in the ISO Intelligent Transport System standards for all communications within the transportation ecosystem. However, standards are not directives or legal requirements; vehicle manufacturers can choose not to implement them, and so far, they have chosen not to.
It's Complex
Although automobile manufacturers have embraced the security standards prescribed by United Nations Economic Commission, Working Party 29, and ISO 21434, which are essential standards, and are necessary from a configuration management and supply chain perspective, these standards do not prescribe a standardized security network architecture. Currently, all vehicle manufacturers are developing their own diverse, non-standardized security architectures for vehicles. As the transportation system becomes increasingly connected, connectivity must become standardized for a safe and efficient transportation system. The vehicle itself cannot be an isolated island in the transportation ecosystem. Managing and maintaining diverse and disparate network security implementations and data formats will make managing the transportation system exponentially more difficult and costly. This is too much of a price to pay for monetizing the data generated by the vehicle owners' use of the vehicles they own and the data generated through their use of their vehicles. Whether an owner jailbreaking the head unit to obtain free XM radio or hacking the code to enable their seat heater is a discussion that needs to be vetted in a policy and governance setting. The aftermarket wants vehicles to be safe and secure and has worked with other transportation system stakeholders to help achieve that goal.
Conclusion
Cyber-attacks are increasing, and vehicle thefts are at record levels. During the pandemic, the automotive aftermarket was identified as an essential service. Consumers deserve safe, secure, standardized security for their vehicles, the choice in who has access to the data generated through their use of the vehicle they purchased, and the right to choose who repairs their vehicle. Giving the customer control of the data is a global trend, and in Europe, there is an ongoing action to regulate this access so that car makers must allow customer control of OBD II data. We should be primarily concerned with the safety and privacy of vehicle owners and implement existing solutions that can meet those objectives by technically implementing policies and governance in accordance with the needs of all transportation system stakeholders. The ISO standards can meet this objective.

Welcome to the new YANG Effect! Your one-stop quarterly newsletter for all things Automotive Aftermarket contributed to and written by under-40 industry professionals.
More posts

Market Insights with Mike is a series presented by the Auto Care Association's Director of Market Intelligence, Mike Chung, that is dedicated to analyzing market-influencing trends as they happen and their potential effects on your business and the auto care industry.
More posts
